🚀 Ph4nt0m 1ntrud3r picoCTF Writeup: Master PCAP Analysis & Base64 Decoding
Learn how to extract hidden flags from network traffic using Wireshark and Python. This guide breaks down the process of analyzing PCAP files, identifying Base64 encoding, and automating the decoding process—essential skills for any cybersecurity enthusiast. Perfect for CTF beginners looking to build a solid foundation in network forensics.
🔍 Introduction
Welcome to the world of network forensics! In this writeup, we are tackling the “Ph4nt0m 1ntrud3r” challenge from picoCTF. We will explore how to find secret messages hidden inside network packets and reconstruct them into a final flag.
- Problem Overview: Analyze a packet capture (PCAP) file to find fragmented data sent by an attacker and restore the original flag.
- Goal: Learn how to use Wireshark for traffic analysis and master the identification and decoding of Base64 strings.
- Target Audience: CTF beginners, students, or developers interested in how data travels across a network.
🛠️ Challenge Overview
You are provided with a .pcap file. This file is essentially a “digital recording” of all data packets that passed through a network interface during a specific period.
- File Provided:
evidence.pcap(or similar) - The Clue: Somewhere within the thousands of packets, there are strings of alphanumeric characters that look like gibberish but follow a specific pattern (Base64).
- The Mission: Locate these fragments, sort them by time, and decode them to reveal the hidden flag.
🔧 Tools Used
To solve this efficiently, we will use the following toolkit:
CyberChef (Optional): A web-based “Swiss Army Knife” for quick data transformations.
Wireshark: The industry-standard GUI tool for inspecting network protocol details.
Python 3: Used for writing a quick script to automate the decoding of multiple data fragments.
🏁 Step-by-Step Guide
🛰️ Step 1: Opening the PCAP file in Wireshark
First, launch Wireshark and open the provided file. When faced with a sea of packets, you need to look for anomalies—specifically, packets with unusual lengths or protocols.
- Open Wireshark and drag the file into the window.
- Scan the Length column. In this challenge, packets with a length other than the standard (e.g., 48 bytes) contain the payload.
- Inspect the Packet Details pane to find strings ending in
=or==.
💡 Explanation:
A PCAP file is a log of network traffic. Attackers often hide data by splitting it into small chunks across multiple packets to avoid detection by security filters. By sorting by length or protocol, you can quickly filter out the “noise” of standard network chatter.
🔠 Step 2: Recognizing Base64 Encoded Data
Base64 is a common way to encode binary data as text.
If you see random-looking letters ending in = or ==, that’s a strong hint that it’s Base64.
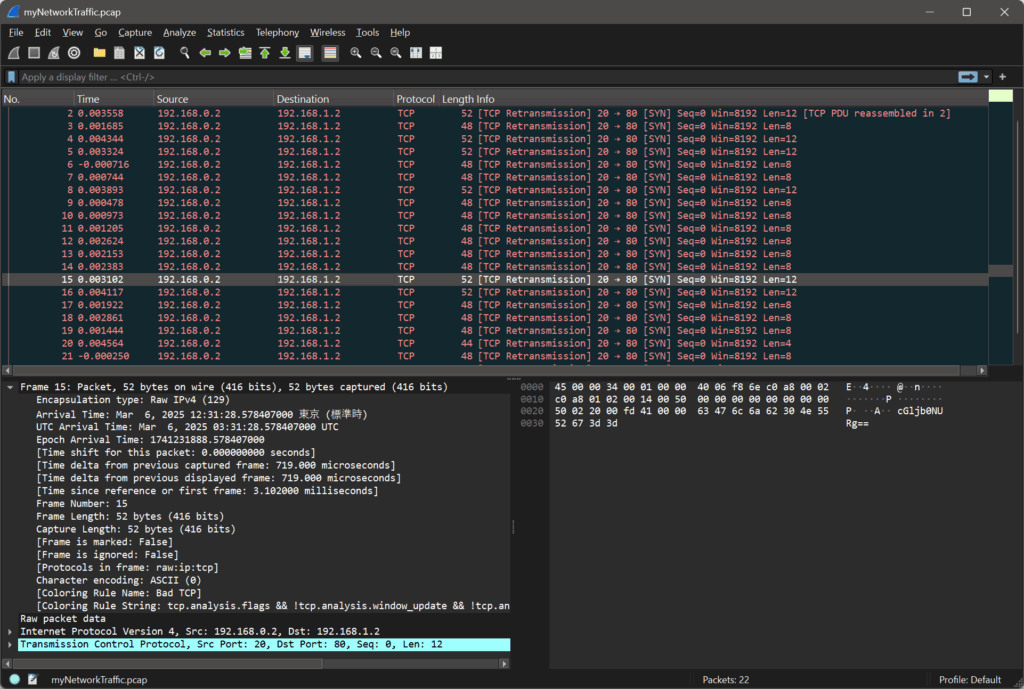
There is a lot of information, so look at length other than 48 bytes.
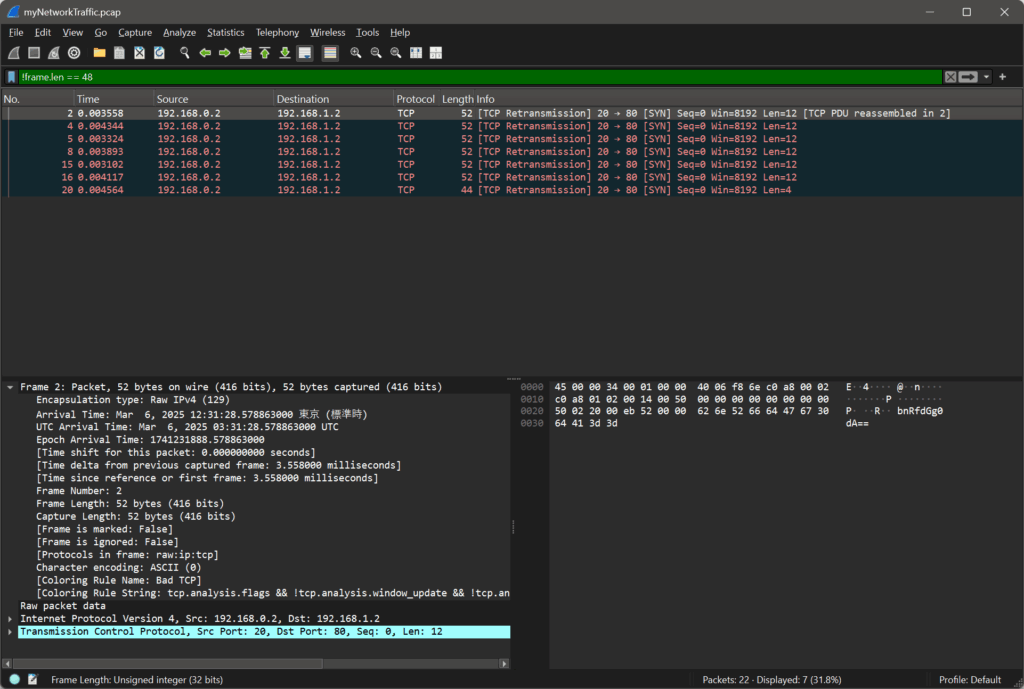
Here’s what some of the captured data looks like:
31.28.5788 bnRfdGg0dA== 31.28.5796 NjZkMGJmYg== 31.28.5786 ezF0X3c0cw== 31.28.5791 XzM0c3lfdA== 31.28.5784 cGljb0NURg== 31.28.5794 YmhfNHJfOQ== 31.28.5798 fQ==
Each line shows:
- A timestamp (the time the packet was captured)
- A Base64 string (the data payload)
💡 Explanation:
Base64 is a binary-to-text encoding scheme. It represents data using only 64 characters (A-Z, a-z, 0-9, +, /). Because Base64 operates on 3-byte blocks, it uses the = sign as “padding” if the data doesn’t fit perfectly. Seeing a trailing equals sign is the #1 tell-tale sign of Base64.
⏱ Step 3: Sorting the packets by time
The data seems out of order, so let’s sort it chronologically by the timestamp:
31.28.5784 cGljb0NURg== 31.28.5786 ezF0X3c0cw== 31.28.5788 bnRfdGg0dA== 31.28.5791 XzM0c3lfdA== 31.28.5794 YmhfNHJfOQ== 31.28.5796 NjZkMGJmYg== 31.28.5798 fQ==
Once we have them ordered correctly, we can decode each Base64 string.
💡 Explanation:
The sequence is critical. If even one fragment is out of place, the resulting text will be unreadable. In forensics, the timestamp is your source of truth for reconstructing an attacker’s actions.
🐍 Step 4: Decoding Base64 in Python
Let’s write a short Python script to decode all these Base64 strings and combine them.
import base64
cipher = [
"cGljb0NURg==",
"ezF0X3c0cw==",
"bnRfdGg0dA==",
"XzM0c3lfdA==",
"YmhfNHJfOQ==",
"NjZkMGJmYg==",
"fQ=="
]
plain = ""
for c in cipher:
decoded = base64.b64decode(c).decode()
plain += decoded
print(plain)
✅ Explanation:
import base64→ loads the Python library for Base64 encoding/decodingb64decode()→ converts Base64 text back into readable ASCII text- The loop joins all decoded parts together into one final string
▶️ Step 5: Running the Script
Run the script in your terminal:
$ python3 decode.py
Output:
picoCTF{1t_w4snt_th4t_34sy_tbh_4r_966d0bfb}
🎉 We’ve found the flag!
🏁 Final Flag
picoCTF{1t_w4snt_th4t_34sy_tbh_4r_966d0bfb}
🧠 Summary
| Step | Tool / Command | Purpose | Key Finding |
|---|---|---|---|
| 1 | Wireshark | View PCAP file contents | Found encoded packets |
| 2 | Base64 | Recognize encoded data | Strings ending in = |
| 3 | Sorting | Order packets by time | Built proper sequence |
| 4 | Python + base64 | Decode data | Revealed flag text |
📖 Short explanations for commands/techniques used
- PCAP (Packet Capture): A file format used to store network data.
- Base64: A method of encoding binary data into ASCII characters to prevent data corruption during transit.
- Wireshark Display Filter: A tool within Wireshark (e.g.,
tcporhttp) used to hide irrelevant traffic. - Python
base64Module: A built-in library that provides functions for encoding and decoding Base64 data.
💡 Beginner Tips
- Look for Padding: Whenever you see strings ending in
=, try Base64 decoding first. It’s the most common encoding in CTFs. - Sort Everything: In network challenges, always check if the data is out of order. Timestamps are your best friend.
- Follow the Stream: In Wireshark, right-click a packet and select “Follow > TCP Stream” to see the entire conversation in a readable format.
🧠 What you learn (takeaways)
- Network Visibility: You learned how data is fragmented across packets and how to view it.
- Pattern Recognition: You gained the ability to spot Base64 encoding at a glance.
- Efficiency through Scripting: You saw how a few lines of Python can replace tedious manual work, a key mindset for any security professional.
📚 Further Reading
Here are related articles from alsavaudomila.com that complement this challenge: