Description
Can you get the flag?Go to this website and see what you can discover.
🧩 Challenge Overview
In this challenge, we are given access to a web instance.
Our goal is to find the login credentials hidden in the HTTP traffic and log in to retrieve the flag.
🖥 Step 1: Open the website and inspect traffic
After launching the instance, we open the website.
We can monitor HTTP communication using Burp Suite, a web security testing tool.
✅ Explanation:
- Burp Suite allows you to see all requests and responses between your browser and the server.
- Navigate to Target → Site map to find the website link.
- Go to Proxy → HTTP History to see all HTTP requests and responses.
🔑 Step 2: Analyze the login page
The site shows a login form.
We try entering random credentials:
username: test password: 1234
The login fails, but Burp Suite shows the HTTP request and response.
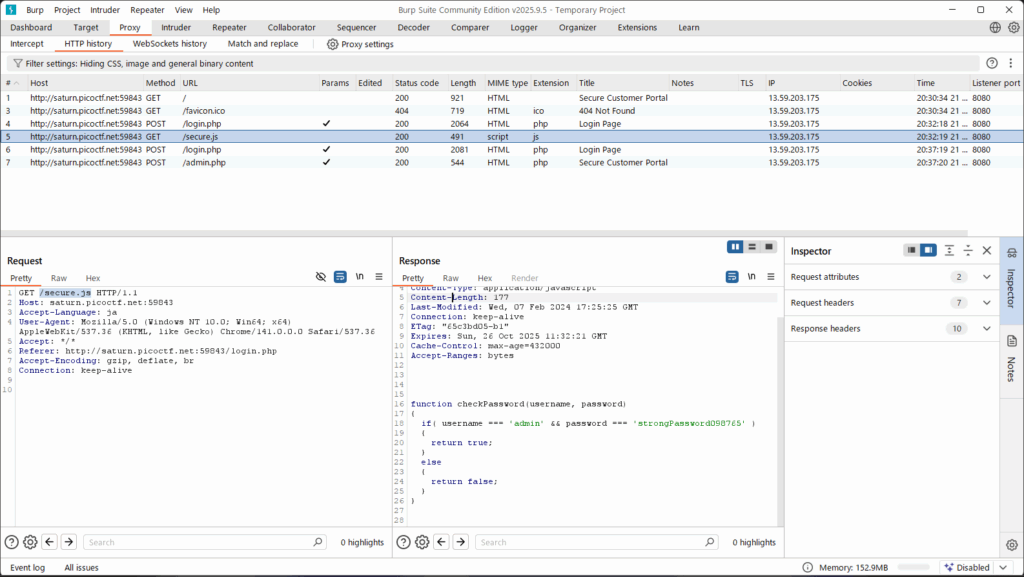
In the response, we find:
function checkPassword(username, password)
{
if( username === 'admin' && password === 'strongPassword098765' )
{
return true;
}
else
{
return false;
}
}
✅ Explanation:
- The JavaScript code reveals the correct credentials.
- This is a common CTF trick — sometimes the front-end code contains hidden information.
📝 Step 3: Log in with the revealed credentials
From the code:
username = 'admin' password = 'strongPassword098765'
Entering these values into the login form allows successful authentication.
🏁 Step 4: Capture the Flag
After logging in, the flag appears:
picoCTF{j5_15_7r4n5p4r3n7_05df90c8}
🧠 Summary
| Step | Tool / Command | Purpose | Key Finding |
|---|---|---|---|
| 1 | Burp Suite | Intercept HTTP traffic | See all requests/responses |
| 2 | Analyze JS | Check for hidden info | Found username/password in checkPassword |
| 3 | Login | Use revealed credentials | Flag displayed |
💡 Beginner Tips
- Use Burp Suite or browser developer tools to inspect HTTP requests and responses.
- Front-end JavaScript sometimes contains sensitive information — always check it in CTFs.
- Look for patterns like
===in JS code — they often indicate conditions for login checks.