Description
Can you get the flag?
Additional details will be available after launching your challenge instance.
🧩 Challenge summary
You open a web instance and inspect its traffic.
By looking at the site and the HTTP requests, you discover that the page’s JavaScript and CSS are stored in separate files. Each file contains part of the flag, and combining them yields the full flag.
🖥 Step 1 — Open the website and inspect HTTP traffic with Burp Suite
After launching the instance and opening the site in your browser, we use Burp Suite to observe what the browser requests and what the server responds.
- In Burp Suite, go to Target → Site map to find the site host and links.
- Then open Proxy → HTTP history to view a list of HTTP requests and responses.
What this does: Burp Suite acts as a proxy between your browser and the web server so you can see every request/response (headers, body, URLs). This is useful to discover linked files (scripts, stylesheets) that aren’t obvious just from looking at the page.
🔍 Step 2 — Interact with the page and notice the button
On the page there is a button:
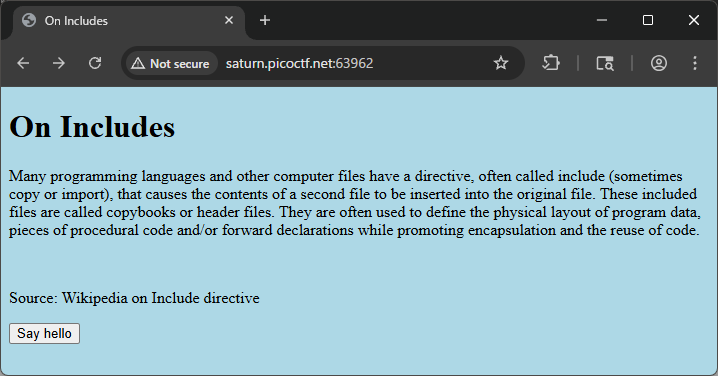
<button type="button" onclick="greetings();">Say hello</button>
Clicking it shows a popup with the text:
This code is in a separate file!
What this means: The page tells us the implementation (the code) lives in an external JavaScript file rather than inline in the HTML. The onclick="greetings()" reveals a greetings() function exists somewhere.
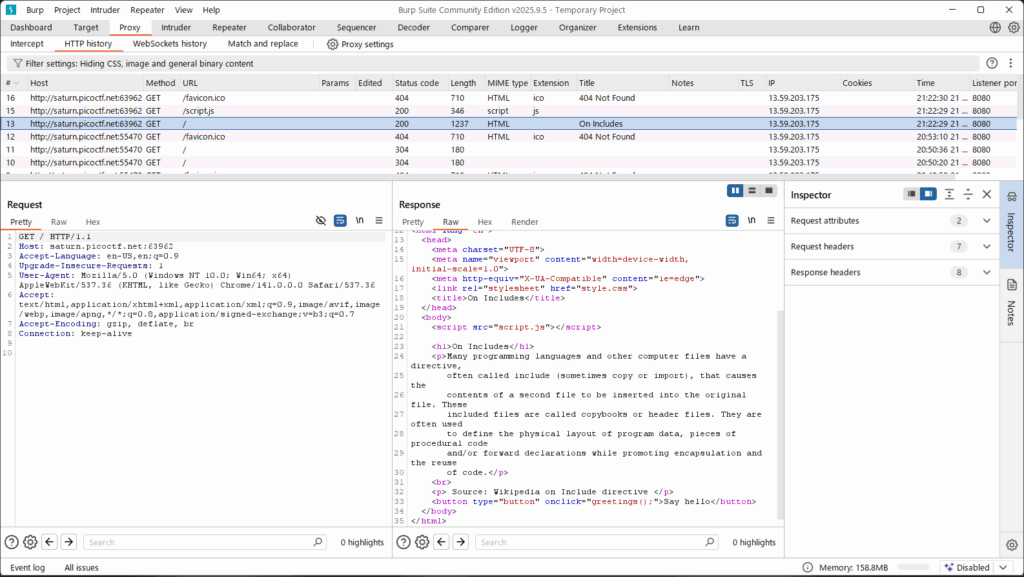
📂 Step 3 — Check the GET responses for linked files
From the HTTP history (or by viewing the page source), you confirm the page loads two files:
/script.js/style.css
Burp (or the browser devtools) shows you can open those URLs and read their contents.
Why: Static assets (CSS/JS) are often linked in the page and can contain hidden hints or text. Examining each linked file is a common CTF technique.
🎨 Step 4 — Inspect style.css
style.css contains normal CSS plus a commented line:
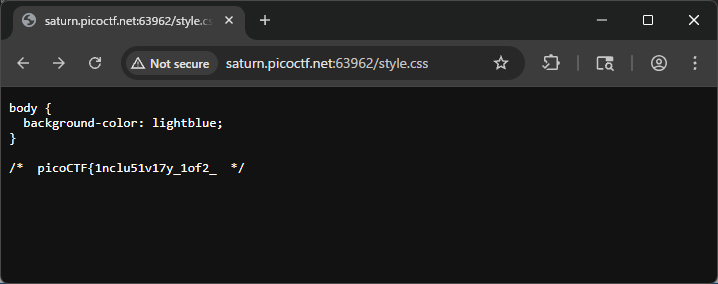
body {
background-color: lightblue;
}
/* picoCTF{1nclu51v17y_1of2_ */
Explanation:
- CSS comments (
/* ... */) do not affect rendering but are visible when you open the file. - Here the comment contains the first half of the flag.
🧩 Step 5 — Inspect script.js
script.js contains:
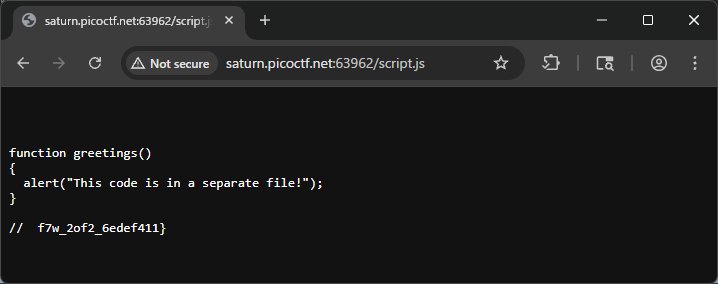
function greetings()
{
alert("This code is in a separate file!");
}
// f7w_2of2_6edef411}
Explanation:
- The
greetings()function just shows the alert when the button is clicked. - After the function there’s a JavaScript comment containing the second half of the flag.
🔗 Step 6 — Combine the two parts
By joining the flag fragments found in the CSS and JS comments:
- From
style.css:picoCTF{1nclu51v17y_1of2_ - From
script.js:f7w_2of2_6edef411}
You get the full flag:
picoCTF{1nclu51v17y_1of2_f7w_2of2_6edef411}
🏁 Final Flag
picoCTF{1nclu51v17y_1of2_f7w_2of2_6edef411}
🧠 Summary
| Step | Tool / Action | Purpose | Key Finding |
|---|---|---|---|
| 1 | Launch instance / Open browser | Access the challenge website | Web page with “Say Hello” button |
| 2 | Burp Suite (Proxy → HTTP History / Target → Site map) | Inspect HTTP requests and resources | Found external files: script.js and style.css |
| 3 | View HTML source | Identify JavaScript function call | onclick="greetings()" |
| 4 | Open /style.css | Check for hidden comments | First half of the flag found |
| 5 | Open /script.js | Check for hidden comments | Second half of the flag found |
| 6 | Combine both parts | Reveal the final flag | picoCTF{1nclu51v17y_1of2_f7w_2of2_6edef411} |
💡 Beginner tips
- Burp Suite (Proxy → HTTP History): Lets you view all HTTP requests and responses between your browser and the server. Great for discovering hidden or linked resources.
- View Source / DevTools: Inspect the HTML to find referenced files (
<script src=...>,<link href=...>). onclickand JS functions: Anonclick="greetings()"indicates a function namedgreetingsexists (maybe in an external JS file).- Check linked files: Open
.jsand.cssfiles — flags are often hidden in comments.- CSS comments use
/* ... */. - JavaScript comments use
// ...or/* ... */.
- CSS comments use
- Combine fragments: Challenges sometimes split flags across multiple files — collect and concatenate the pieces in order.