Description
The Network Operations Center (NOC) of your local institution picked up a suspicious file, they’re getting conflicting information on what type of file it is. They’ve brought you in as an external expert to examine the file. Can you extract all the information from this strange file?Download the suspicious file here.
🧩 Challenge Description
In this challenge, we are given a PDF file, and part of the flag can be seen inside it.
The hint suggests that the content may actually be stored in a different file format.
Part of the flag appears in the downloaded PDF file.
1n_pn9_&_pdf_90974127}
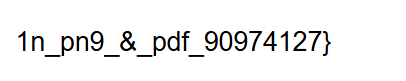
🔎 Step 1: Examine the file type
We can use the file command to identify the real type of the PDF:
$ file flag2of2-final.pdf flag2of2-final.pdf: PNG image data, 50 x 50, 8-bit/color RGBA, non-interlaced
✅ Explanation:
filechecks the magic number (binary signature) of a file to determine its type.- Even though the file has a
.pdfextension, it’s actually a PNG image.
🖼 Step 2: Rename the file with the correct extension
Since it’s a PNG image, we can simply copy it and rename it:
$ cp flag2of2-final.pdf flag2of2-final.png
✅ Explanation:
cpcreates a copy of the file with a new name.- This allows us to open it as a PNG image, which can be viewed with any image viewer.
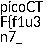
👀 Step 3: Combine the partial flags
By opening the PNG file, we can see part of the flag.
Combine it with the partial flag from the original PDF to get the complete flag:
picoCTF{f1u3n7_1n_pn9_&_pdf_90974127}
🏁 Step 4: Capture the Flag
picoCTF{f1u3n7_1n_pn9_&_pdf_90974127}
🧠 Summary
| Step | Command | Purpose | Key Finding |
|---|---|---|---|
| 1 | file | Check file type | PDF is actually a PNG image |
| 2 | cp | Rename file | Created flag2of2-final.png |
| 3 | Open image | View hidden content | Revealed remaining part of the flag |
💡 Beginner Tips
- File extensions can be misleading — always check with
filefirst. - Some CTF challenges hide content in a different format than the extension suggests.
- Combining partial flags from multiple files is a common trick in forensics challenges.